Research
Detecting face morphs and disentangling identities used in creating morph
Face morphing strategically mixes two or more face images such that the composite image matches successfully to all constituents in terms of biometric utility. Therefore, a morphed face image can be utilized adversarially in an identification document and poses a security threat. We proposed a conditional identity disentanglement network using a GAN that not only performs differential face morph detection guided by a trusted non-morphed reference image but also recovers the second identity used in creating the morph. Check this video to know more about Conditional Identity Disentanglement for Differential Face Morph Detection!
Camera sensor identification for biometric images
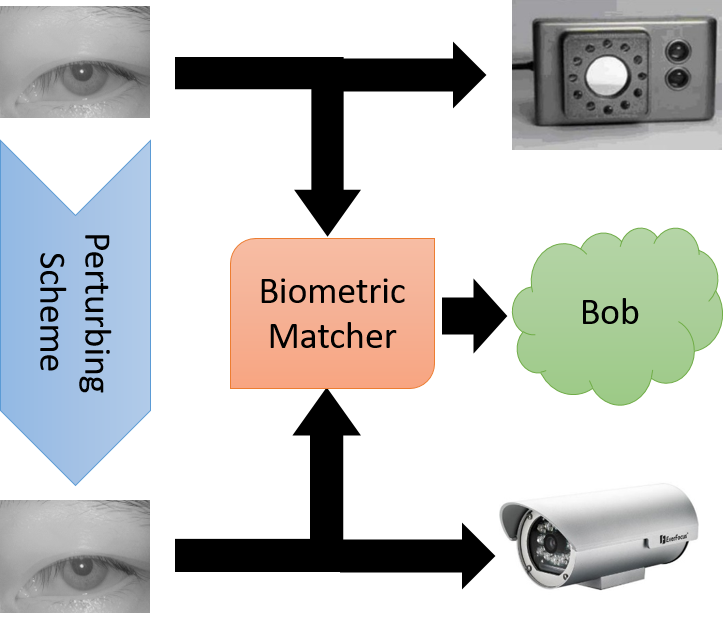
Photo Response Non-Uniformity (PRNU) has been successfully utilized for sensor identification in the literature and is important in the context of image forensics. PRNU manifests as a consequence of artifacts associated with the sensor fabrication process. In iris biometrics, the images are captured using iris sensors typically operating in the near-infrared spectrum, which differ from conventional RGB sensors employed in the camera. Also, the iris images can be subjected to some pre-processing schemes, such as photometric modifications to aid in iris recognition. We evaluate different PRNU schemes in the context of iris sensor identification. We further analyze the impact of photometric transformations known to improve iris recognition performance on PRNU based sensor identification. In many image forensic applications, one can implicitly link the camera with the photographer. This raises privacy concerns, which can be mitigated via sensor de-identification. In this context, we deliberately perturb the image such that the PRNU based sensor classifier incorrectly assigns the modified image to a different sensor but without compromising the utility of the images. In our work, we aim to confound the iris sensor classifier, whilst preserving the iris recognition performance. Check this video to know more about Exploring Vulnerabilities of PRNU-based Camera Fingerprinting!

Deducing the structure of evolution between a set of near-duplicate images
An image can undergo a sequence of photometric or geometric transformations such as, brightness and contrast adjustment, rotation, scaling, etc. to yield a set of near-duplicate images related to each other. Deduction of the hierarchical structure of evolution can be used in the context of image forensics and it is particularly useful in current times due to plethora of image editing tools and software. We develop a method which accepts as input a set of near-duplicate images, and estimate the pair-wise transformation parameters using a parameterized model that employs basis functions. We further utilize the estimated parameters to obtain the relationship and depict it in the form of an Image Phylogeny Tree. The IPT is a directed acyclic graph which indicates the root node (original image) and the child nodes (transformed images) and how they are related to each other. Our method works on near-duplicate face and iris images that have undergone manual as well as automated transformations.
Cyberattack pattern analysis
Defacement of webpages via insertion of graphics and text leads to denial of service attacks and causes financial setbacks to commercial websites. Cyberattacks can be malicious or inocuous depending on the intent of the attacker. Some attackers target specific websites and are active across multiple years. In this work, we perform a longitudinal analysis on web defacement data curated across six years (2012-2017) to detect any discernible pattern in the cyberattacks using machine learning algorithms. This is an interdisciplinary project in collaboration with the Department of Communication, Arts and Sciences and School of Criminal Justice to help understand the human factors in cybercrimes.
- © Sudipta Banerjee
- Design: HTML5 UP